Reviewing Microsoft Cloud App Security Reports on G Suite Identities
Download Sample M365 Risk AssessmentAUTOMATING ONBOARDING STUDENTS AND USING MICROSOFT TO MANAGE G SUITE
PART 4: REVIEWING MICROSOFT CLOUD APP SECURITY REPORTS ON G SUITE IDENTITIES
PROBLEM
The typical IT admin in this scenario requires their School Information System (SIS) to synchronize student data their on-prem AD, Azure AD, and G-Suite. Currently, they feel that neither Microsoft nor Google has provided them with a convenient method with which to both effectively and efficiently manage the identities in these seemingly disparate environments
OBJECTIVE
By integrating Azure Active Directory with G-suite, we will be able to administratively manage an organization's on-prem AD, Azure AD, and G-suite identities from a single portal. In addition, with G-suite's identity management being delegated to Azure AD, we can redirect the SIS's synchronization from G-suite to either the on-prem AD or Azure AD.
In this way, we will have a continuous stream of data flowing from one entry point, that is reflected in all relevant directories. Such a seamless system will make the provisioning of identities, access permissions, and group memberships a simple process for IT administrators.
PART IV: REVIEWING MICROSOFT CLOUD APP SECURITY REPORTS ON G SUITE IDENTITIES
In this section we will be highlighting the following items:
- Monitoring G Suite Identities with Microsoft Cloud App Security (MCAS)
- Overview of Microsoft Cloud App Security Reports
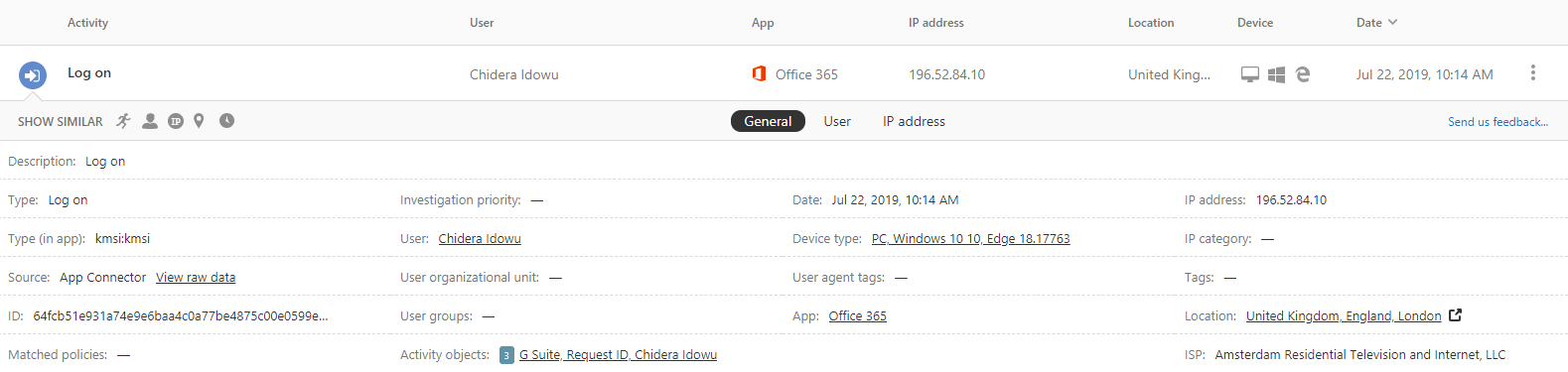
With our G Suite Identities being managed by Azure AD, we also gain instant visibility into the sign-in activity log of our G Suite Users.
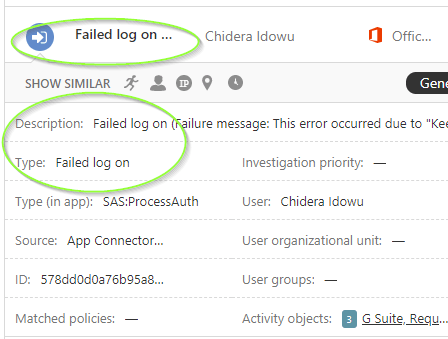
Firstly, from the screenshot above that was taken from our MCAS activity log , we can see that the user was successfully able to complete his login, as a failed login would indicate a failed attempt in both the Description and Type field.
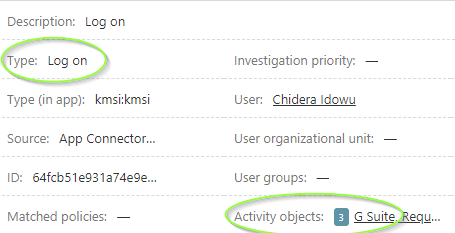
Taking a closer look at the activity details of this user, we can see that this logged activity was a log on attempt to our G Suite app for which Azure AD SSO was configured:
Looking farther to the right of the expanded activity view of this user, we can also garner additional information on the type of device that was used to login to G Suite, and the location from which the user’s connection is originated:
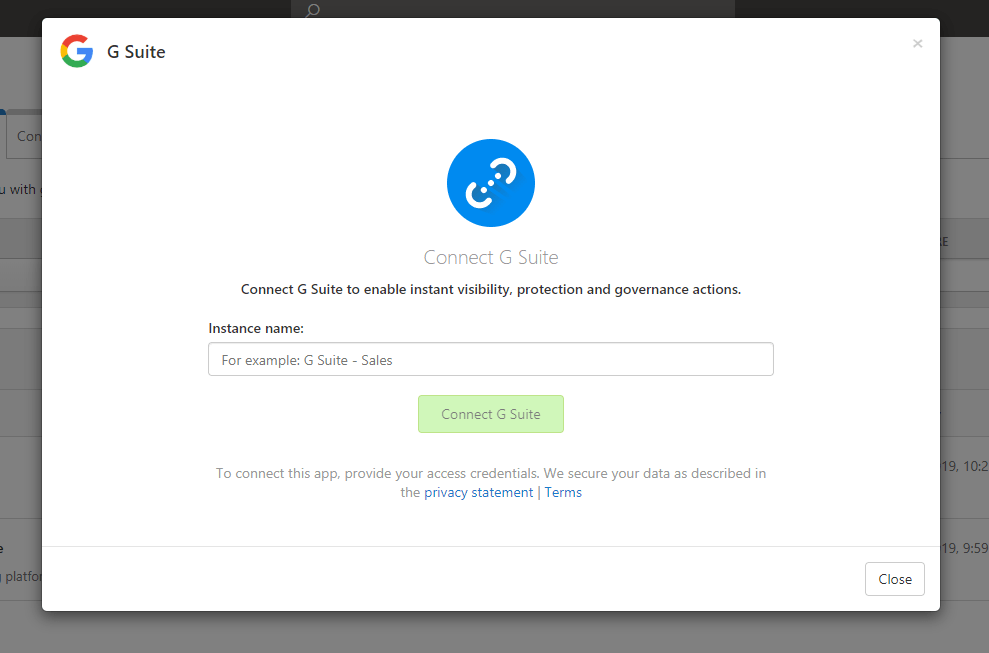
Now this is but a fraction of the oversight and management of G Suite identities that can be had with Microsoft Cloud App Security. By adding G Suite as one of our connected apps directly through the MCAS portal, we can gain even more administrative control over our G Suite accounts and data:
With that said, reviewing the MCAS logs for our G Suite identities once we have Azure AD managing them is a great place to start to acquire some familiarity with its capabilities.