As mentioned in my previous blog titled “Microsoft Azure: Networking Basics”, subnets carved out from a VNET address space have complete access to communicate with one another. Although there’s more than one way to control cross network communication, this blog will cover the method of using Network Security Groups (NSG) to achieve this goal.
NSGs can be deployed through the Azure Marketplace and associated to either a subnet, VM network interface or both. When applied to the subnet, all VM’s contained within its network range will be impacted by the NSG. Applying the NSG directly to a VM interface can provide access control on a per VM level. Note that a VM that has an NSG applied to its virtual interface will still be impacted by a separate NSG at the subnet level.
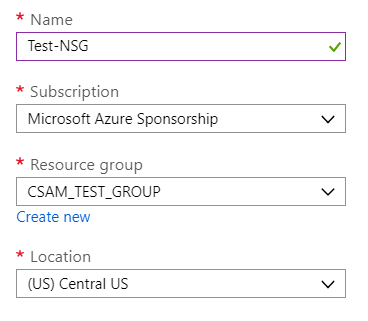
During the initial NSG creation process, you will be asked to fill in the name for your new NSG object as well as its resource group. The resource group is a logical container for Azure objects to exist in and can be one that you’ve already created or a newly provisioned group.
Configuring & Applying A Network Security Group
Once deployed from the Azure Marketplace, you can now configure the inbound and outbound security rules and associate the NSG to either a subnet or VM interface.
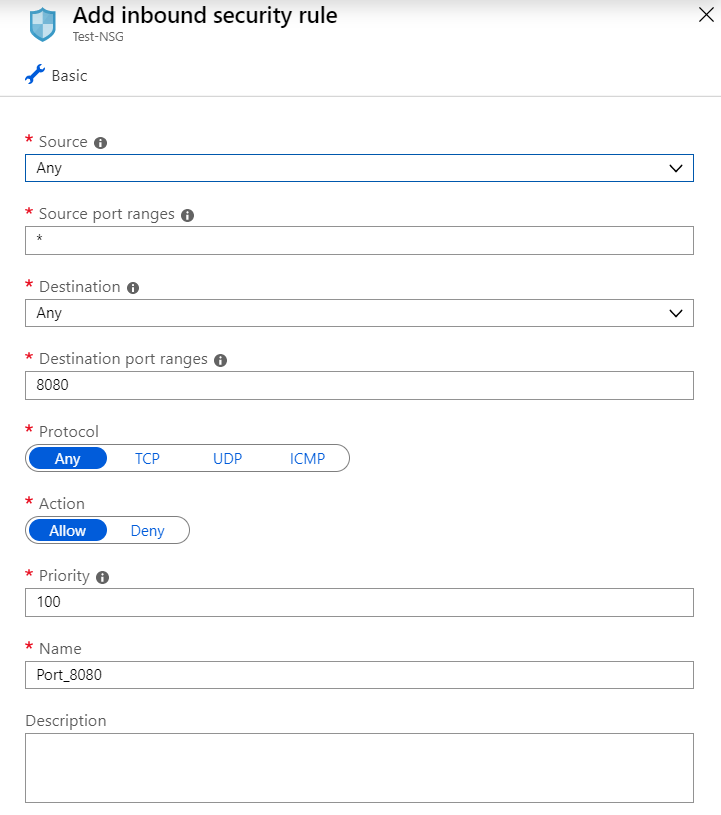
Security rules use a combination of source and destination addresses or networks, port ranges, and protocols. Also note that just like access control lists, the rules are processed from a top to bottom order based on its priority number.
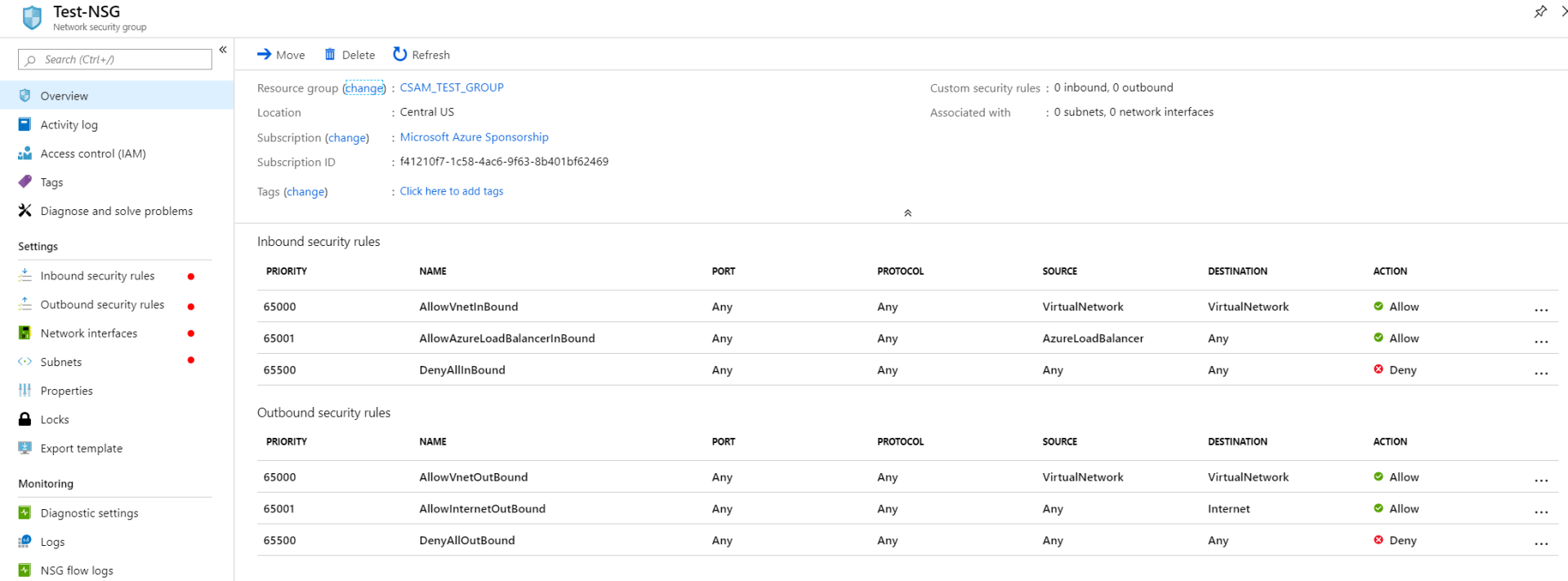
Options to configure security rules and association to a subnet or network interface can be accessed from the menu show below.
Once associated to a subnet or network interface, it can take several seconds to take effect. Inbound and outbound security rules must also be configured in their respective menu options. Configuring a rule meant for outbound traffic under the inbound section for example could result in unintended filtering of network traffic.
It’s also worth noting that if a VM has a public IP directly associated to its network interface, the NSG can be used to control and filter traffic between the VM and internet sources (as long as a UDR isn’t being used to route internet traffic through a virtual security appliance). In this scenario, an NSG applied to the VM interface would be used.