IT Security
Blog Articles
CATEGORIES
Protect your business data in the cloud with Microsoft Office 365, but be aware of retention limitations in Outlook, Exchange Online, OneDrive, and SharePoint.
Explore the lessons learned from Delta Airlines' network collapse, emphasizing the necessity for businesses to invest in fail-over systems and prioritize IT resiliency to avoid costly downtime.
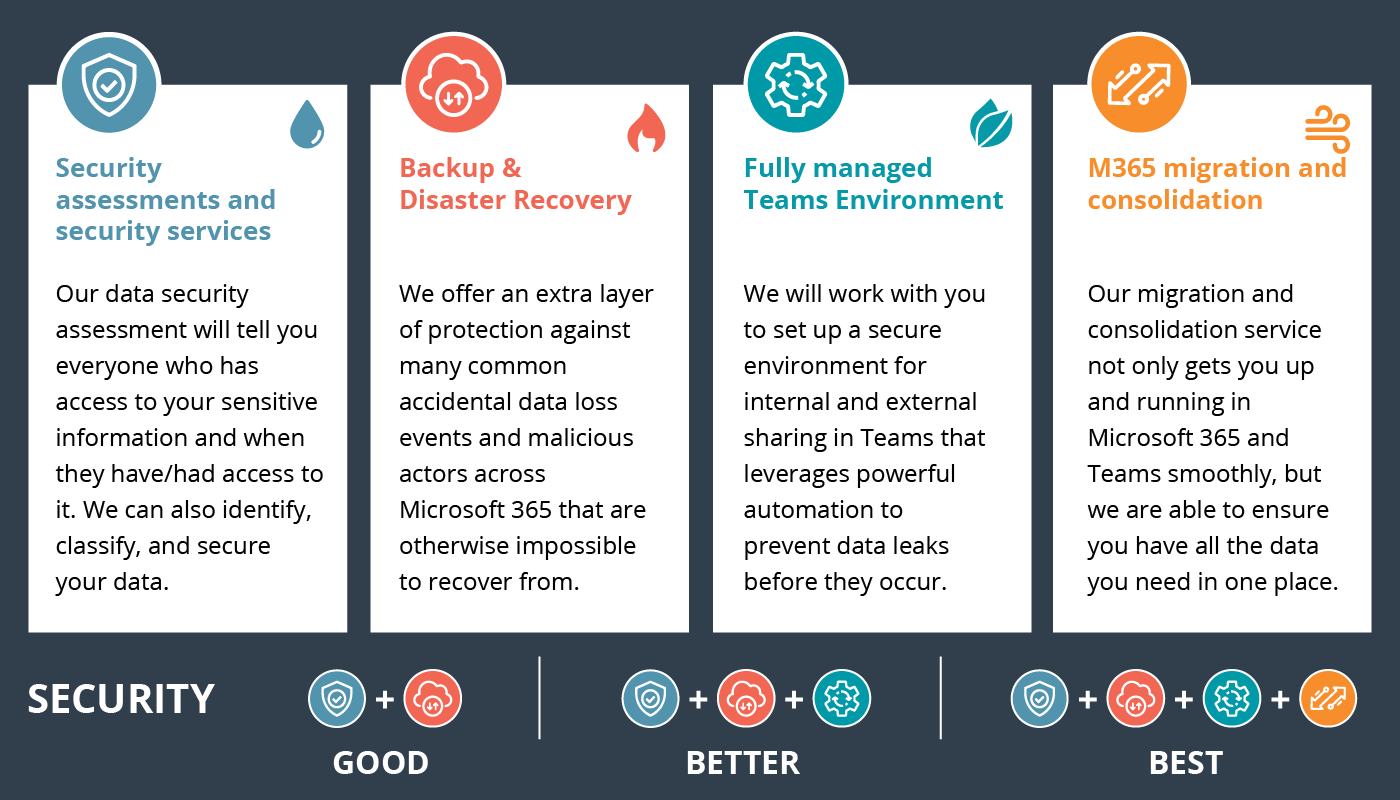
Discover the benefits of cloud-based security, including ease of deployment, performance, and scalability, while reducing the risk of human error and data breaches. The cloud is not inherently insecure, as traditional on-premise IT systems have experienced more massive data breaches.
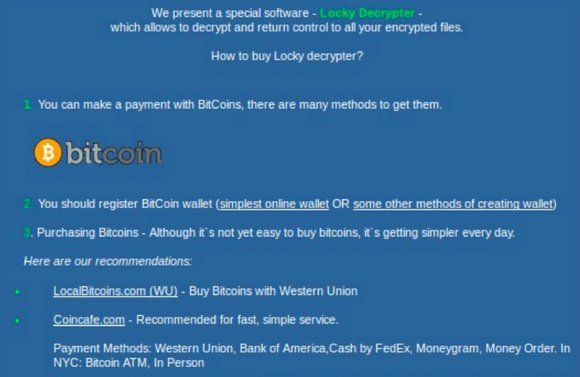
Worried about ransomware? Take action now! Back up your data, prevent files from running in specific folders, unhide file extensions, filter out executable emails, disable Remote Desktop, and regularly update your software to stay one step ahead of cyber threats.
Forget your PINs? Create a memorable emoji story for a secure and easy-to-remember password.
Compliance with regulatory laws is crucial for businesses dealing with sensitive data. Avoid identity theft, fines, and imprisonment by adhering to regulations like PCI DSS, HIPPA, and SOX. Protect your business, customers, and reputation by staying compliant.
Learn how a VPN can help you bypass censorship, protect your online activity from monitoring, and access restricted content from anywhere in the world.
Importance of strong passwords and passphrases in preventing unauthorized access to files, programs, and resources.