Hacking is everywhere. With every day, a new major cyber attack hits the headlines. The other day, HBO was attacked, and hackers not only release unaired episodes of shows like Ballers, but also scripts from Game of Thrones and personal phone numbers of the stars. More will be released if HBO refuses to pay a ransom, according to the hackers.
THE BOUNTY
This isn’t unusual. Target, Sony, Home Depot, LinkedIn, Netflix: Hackers go after the biggest and the best, hoping to blackmail money or steal the financial data from customers. And they do it because those companies are huge. HBO could pay a couple million dollars to gets its content back.
But those are the big headlines, and that doesn’t mean hackers don’t shop local.
ATTACKS CLOSE TO HOME
Recently, a 10th-grader hacked into a Texas school and changed grades for those who paid him. It is a simple function of the internet: If you have the knowhow, you can breach weak systems.
But it isn’t just the grade-changing David Lightman’s, from War Games, of the world who are taking a deep dive into the schools’ cyber networks. The attacks on colleges and universities are systemic.
Last year, 13% of educational institutions experienced a ransomware attack. That’s an astounding number mainly because of the implications. Schools have an enormous wealth of private data on students, including social security numbers and financial information. Many schools have health facilities with private health information for students. Likewise, some of the most innovative research happens at universities around the world, and hackers (state-backed or otherwise) can steal R&D out from under the players.
The question many organizations are asking themselves is whether or not their current cybersecurity systems will maintain integrity when a breach occurs. There’s no way to know unless you test it. Well, there’s one other way to find out if your cybersecurity is weak…
FIND OUT YOUR SECURITY SCORE
The first thing you should do is get your security score. Anyone who has admin permissions (global admin or a custom admin role) for an Office 365 Business Premium or Enterprise subscription can access your secure score here. This will give you a general idea of how secure your network is. It's also a good idea to perform security audits consistently to find potential threats or weak areas in the network.
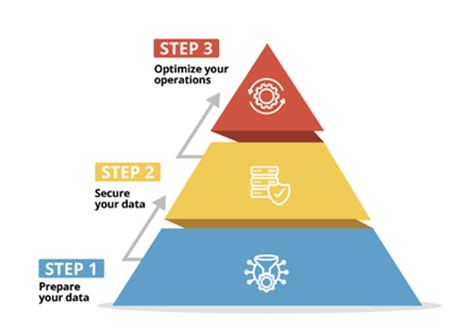
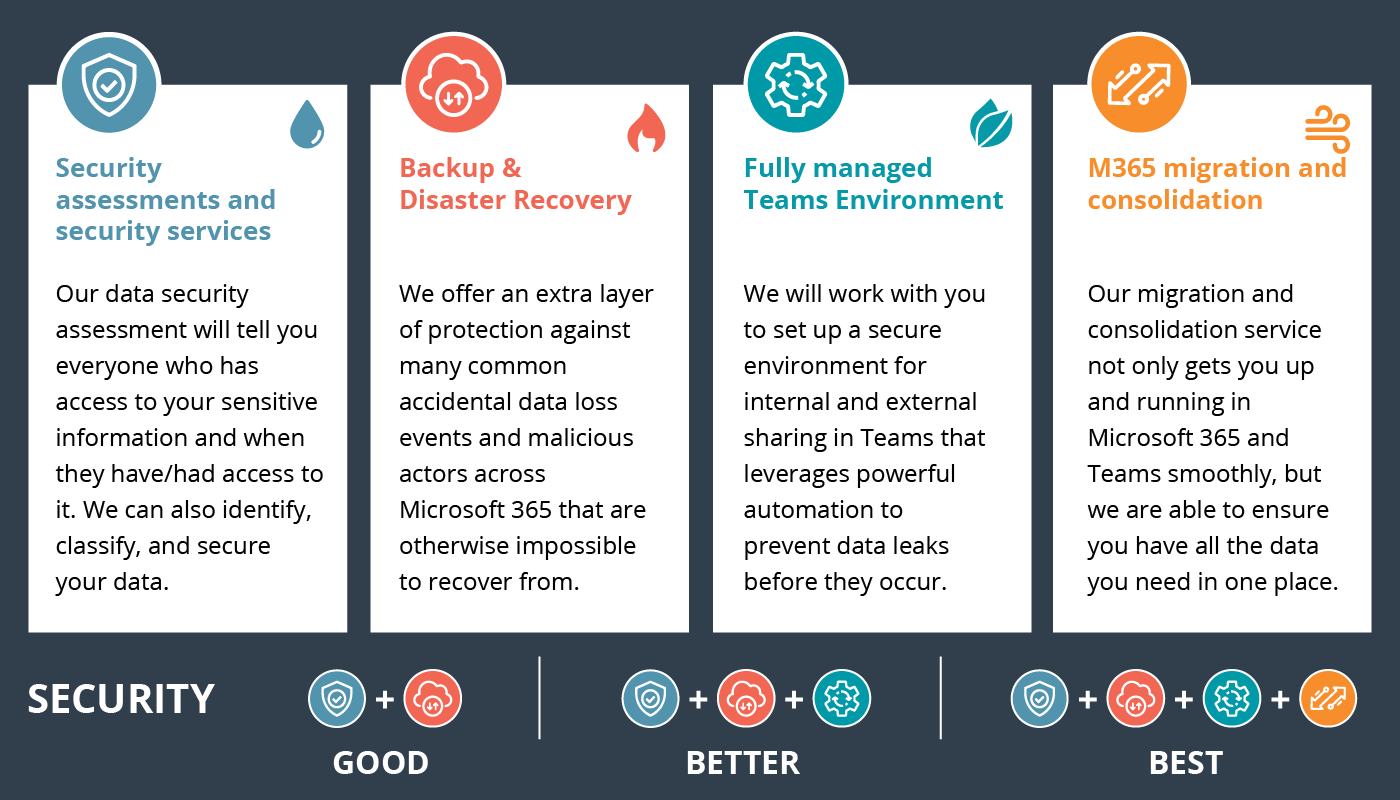
THE AKINS IT METHOD
Security assessments are a huge component to the Akins IT method of cybersecurity. You must fully understand your network before you can make a plan. Our years of assessing networks have given us a unique perspective on the needs of the modern learning environment.