Automating Onboarding Students Using Microsoft to Manage Google Workspace Part 2 (Configuring Conditional Access for Google Workspace)
Download Sample M365 Risk AssessmentPart 2: Configuring Conditional Access for Google Workspace
Problem
The typical IT admin in this scenario requires their School Information System (SIS) to synchronize student data their on-prem AD, Azure AD, and G-Suite. Currently, they feel that neither Microsoft nor Google has provided them with a convenient method with which to both effectively and efficiently manage the identities in these seemingly disparate environments
Objective
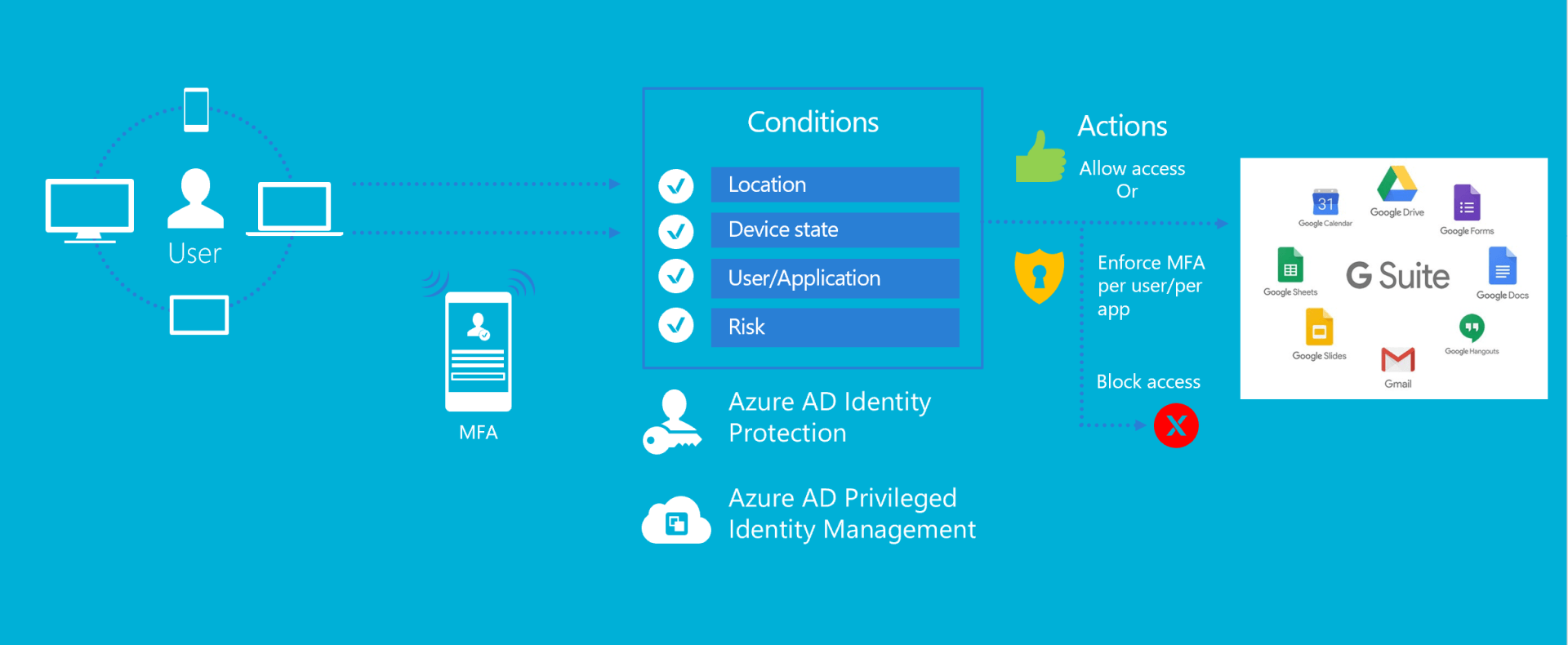
By integrating Azure Active Directory with G-suite, we will be able to administratively manage an organization's on-prem AD, Azure AD, and G-suite identities from a single portal. In addition, with G-suite's identity management being delegated to Azure AD, we can redirect the SIS's synchronization from G-suite to either the on-prem AD or Azure AD.
In this way, we will have a continuous stream of data flowing from one entry point, that is reflected in all relevant directories. Such a seamless system will make the provisioning of identities, access permissions, and group memberships a simple process for IT administrators.
PART II: CONFIGURING CONDITIONAL ACCESS FOR G SUITE
In this section we will be pivoting to the following items:
- Overview of Conditional Access
- Sample CA Policy for MFA based on Location
- Review of Student’s Login Experience
The Conditional Access (CA) policy that we will be creating for our students in this example will be based on location. The intended result of this CA policy is to challenge individuals who attempt to log into G Suite from a location that is outside the school’s campus.
The steps to create this CA policy include:
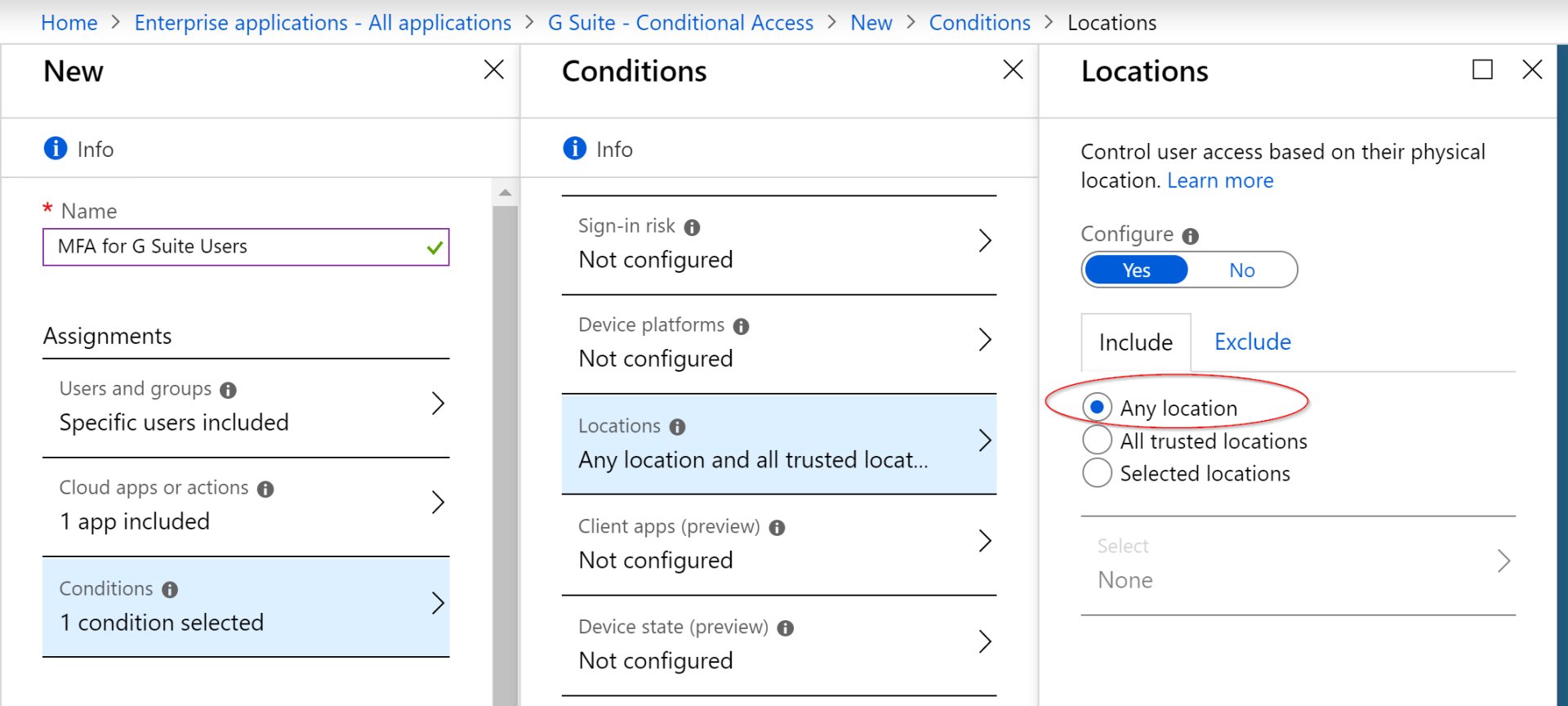
- Name the CA policy
- Specify the security group that we assigned to our G Suite SSO app
- Select G Suite as our Cloud app
- Designate Any location to be Included in this policy
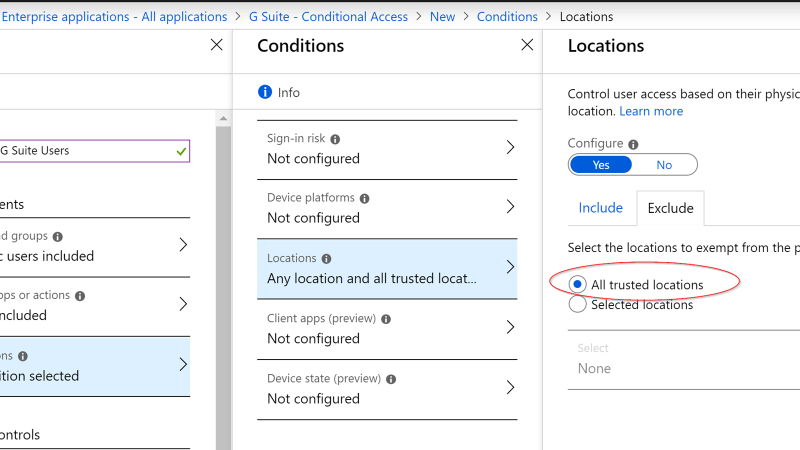
- Exclude – All trusted locations
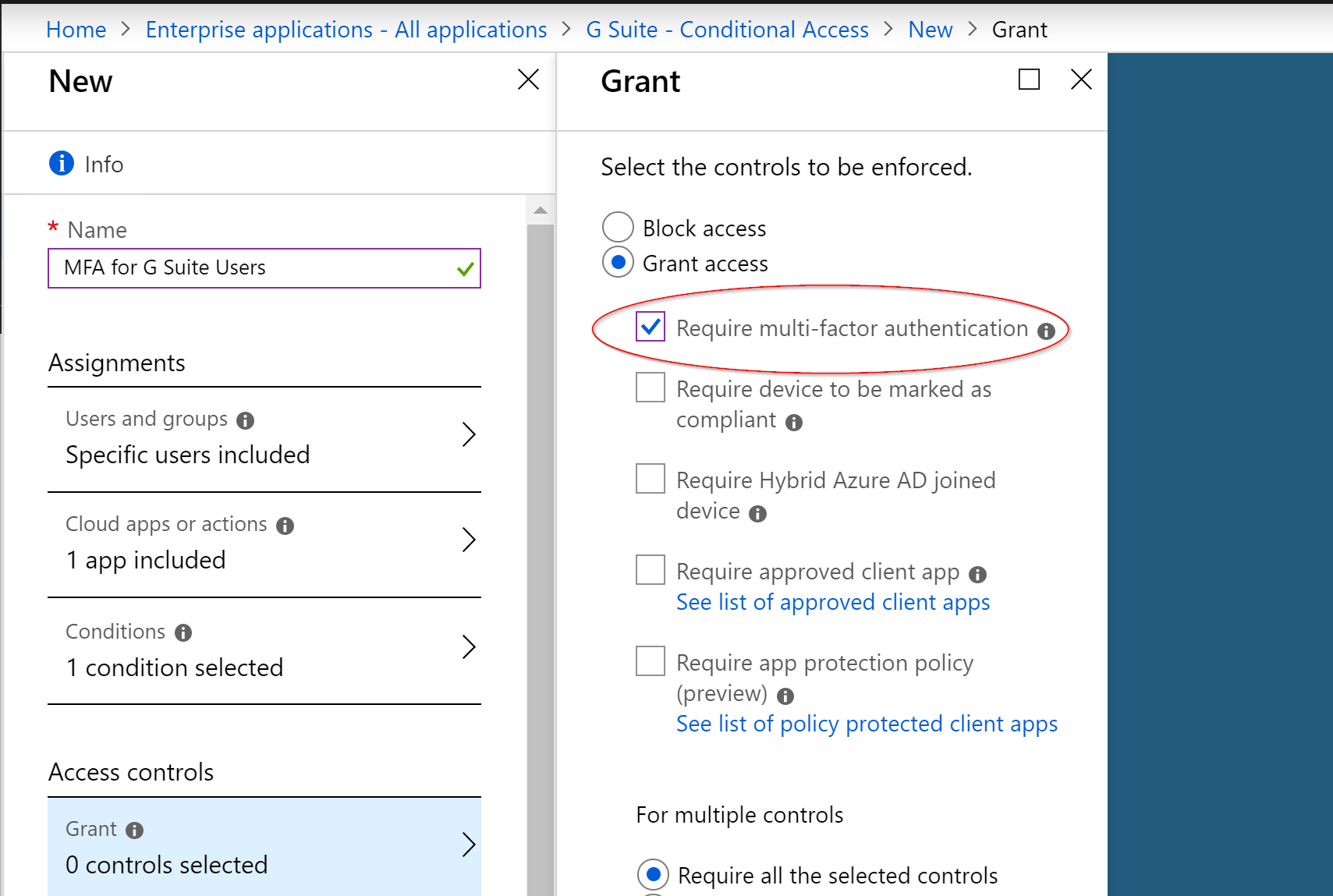
- Select Require multi-factor authentication for the controls to be enforced in order to Grant access
- Selected option to include any location in CA policy
- Excluded All Trusted Locations from this CA policy
- In this way, users will not be prompted to MFA while on the school’s premises
- Access to G Suite resources will still be granted to those users who are outside of the school’s premises, but they are required to authenticate with MFA
With Azure AD now managing the identities in G Suite, we can take advantage of the powerful tools in Microsoft’s arsenal for protecting those identities. By applying Conditional Access and MFA on those identities, we will be ensuring that users are only being challenged when attempting to login from untrusted locations, such as when they are off campus.
CREATE CONDITIONS FOR LEARNING- LEARN MORE ABOUT INTUNE FOR EDUCATION
Solve Your IT Challenges
Increase your network's uptime and keep your connections secure with Akins IT
Attend An Event
Attend one of our events to learn something new from our partners and experts
Solve Your
IT Challenges
Increase your network's uptime and keep your connections secure with Akins IT.
arctic wolf labs
threat report 2024
This report offers expert insights into attack types, root causes, top vulnerabilities, TTPs, and more.
1301 Dove Street #130
Newport Beach, California 92660
Mailing Address:
3406 Via Lido, Suite 1A-22
Newport Beach, California 92663

All Rights Reserved | Akins IT | Privacy Policy | Terms of Service | Disclaimer
Website By: EnlightWorks